Background
For all cryptocurrency enthusiasts, the world of Web3 is filled with opportunities, challenges, and crises. Every day, a multitude of new token projects hit the market, seemingly offering endless chances for wealth, but in reality, potential risks lurk everywhere. With a constant emergence of risky ventures, users are often caught off guard. In such a scenario, how should we assess the reliability of a project and avoid the perils of Rug Pulls to safeguard our finances? Don’t worry, this article will provide you with a comprehensive methodology to judge Rug Pulls, enabling you to minimize the risk of asset loss.
1. Understanding Basic Tools for Crypto Security: Essential Tips to Prevent Rug Pulls
Observe Trend Charts and Verify Trading Volume
Utilize multi-chain DEX crypto analysis tools, such as DEX Screener, and by observing token trend charts, we can spot any abnormal buy and sell ratios to avoid fake trading volumes created by shady projects. Similarly, for newly launched tokens, be alert if you notice suspiciously high trading volumes and large transactions.

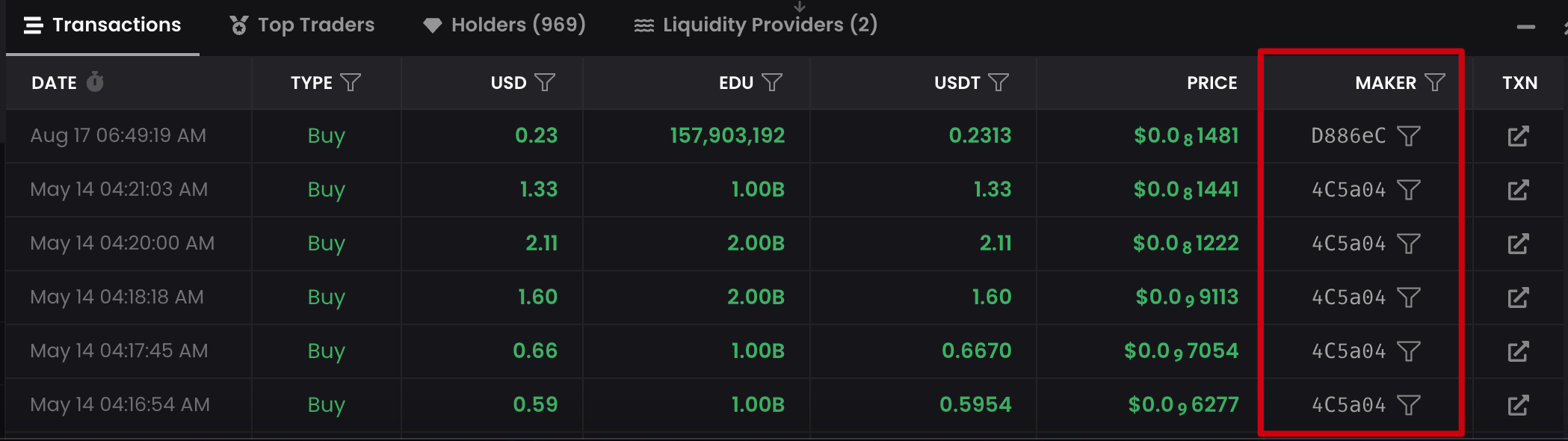
Check Transaction Records
Tools like DEX Screener can list all transaction records, allowing us to simply review the addresses involved in all buy and sell operations. If you discover the same address frequently transacting (as shown in the image), this is also a very suspicious signal.
Use Honeypot and Token Risk Monitoring Features
Platforms including DEX Screener and Advantis.AI offer Honeypot tests and some basic token risk monitoring features, which also assist users in assessing investment risks. As shown, when a user searches for a particular Token, the platform automatically provides the Token's risk level, allowing users to decide whether to withdraw funds in a timely manner.

2. How to Use MetaSleuth for Detecting Rug Pulls in Cryptocurrency Investments
Examine the Deployer's Source of Funds
For a token, aside from the contract address of the token itself and the trading pair address, the Deployer’s address is also crucial. By observing this address’s financial relationships on the blockchain, we can better assess the risk of a project.
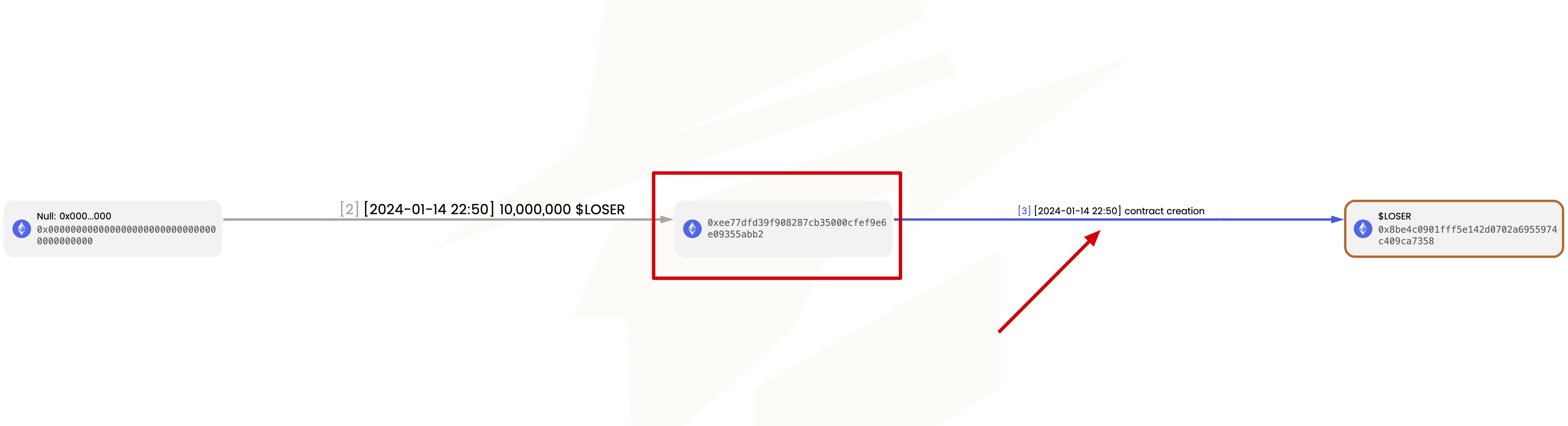
To find the deployer’s address, simply enter the token’s contract address into metasleuth.io. In the generated flowchart of funds, look for the 'contract creation' edge. The transaction at this edge is the creation transaction for the token contract, and the initiator of the transaction is the deployer. Then, you can further analyze the deployer's source of funds.

To effectively avoid risks, users can pay attention to the following common sources of deployer funds, which may indicate high risk:
-
Funds originating from coin mixing services or no-KYC flash swap services (such as Fixedfloat). This is a method chosen by malicious token deployers to avoid being traced back to their real identity.
-
Funds with other illegal sources. The image below shows a Rug Pull network, where all the tokens underwent Rug Pulls in a very short time span. Scammers use the profits from the last Rug Pull to transfer funds to the next address, which then deploys a new token and lures new victims.

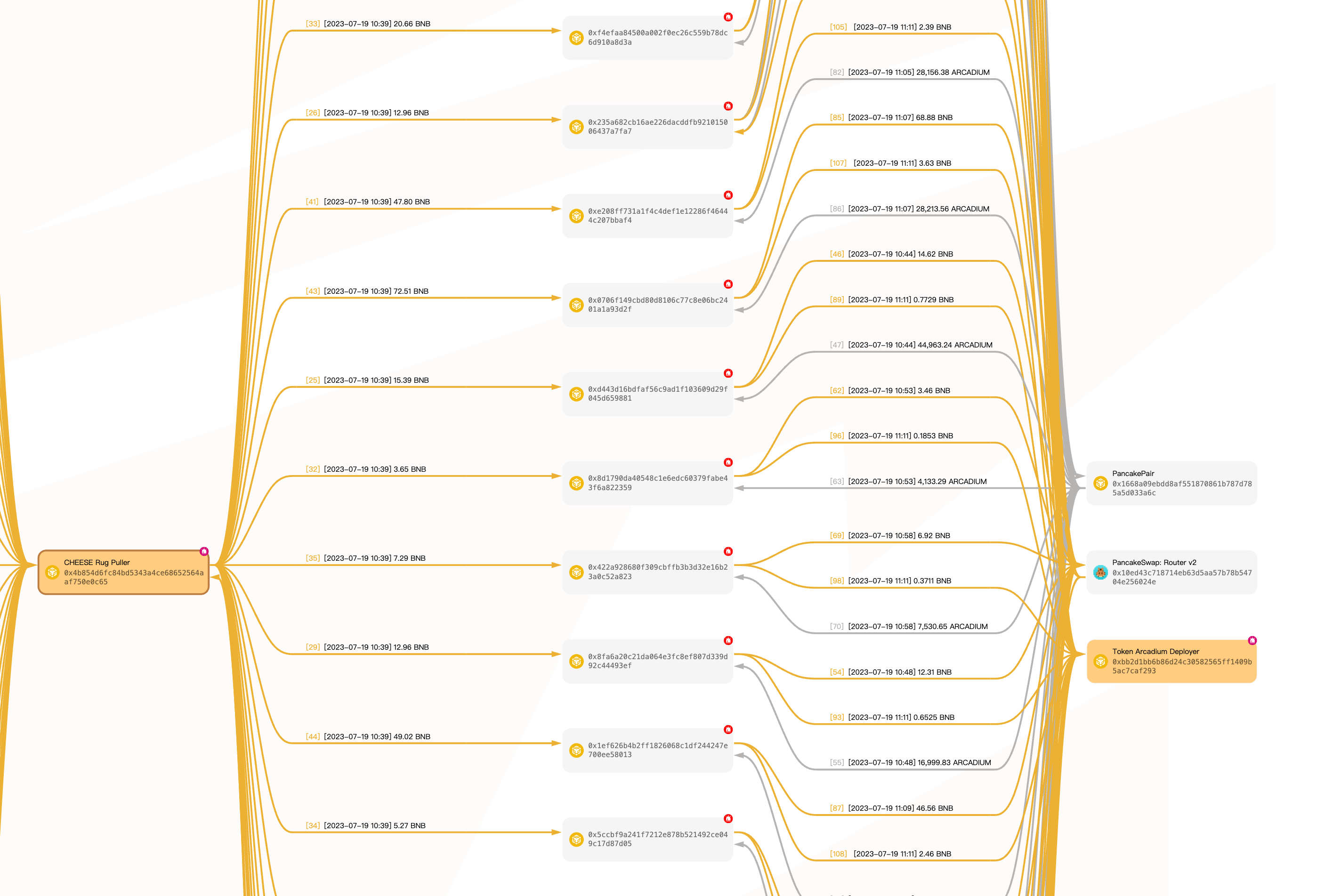
Check Liquidity Sources
Scam project operators are highly skilled at creating false liquidity, as illustrated below. They spread the profits from previous gains across many different addresses. Some of these addresses are only used to buy tokens, while others are tasked with selling tokens. This falsely constructed liquidity entices victims into believing the token is highly popular, not knowing that they will be defrauded once they invest.
Keep an Eye on Top Holders
The image below depicts a list of a token's Top Holders, with the second-ranked holder possessing an amount nearly equivalent to the liquidity pool. This means the holder has the capability to withdraw all funds from the pool at any time.

By further tracking the address’s source of funds in MetaSleuth, we can discover that the address is the token’s deployer, who minted a large number of tokens for themselves at the time of contract creation. Such projects carry extremely high risks.
Summary
Prior to investing, users should conduct proper Due Diligence (DYOR), utilizing mature analysis platforms (such as DEX Screener) and funds tracking platforms like MetaSleuth to aid in investment decisions and to maximally evade risks. Observing trend charts and verifying trading volumes, checking transaction records are among the common methods used. Moreover, tools like MetaSleuth can be instrumental in tracking the deployer’s source of funds and liquidity sources, serving as an effective way to avoid risks. Ensuring the authenticity and reliability of token projects can help cryptocurrency enthusiasts make wiser investment decisions, thus achieving better returns and reducing risks in the Web3 world.
About MetaSleuth
MetaSleuth is a comprehensive platform developed by BlockSec to assist users in effectively tracking and investigating all crypto activities. With MetaSleuth, users can easily track funds, visualize fund flows, monitor real-time fund movements, save important information, and collaborate by sharing their findings with others. Currently, we support 13 different blockchains, including Bitcoin (BTC), Ethereum (ETH), Tron (TRX), Polygon (MATIC), and more.
Website: https://metasleuth.io/
Twitter: @MetaSleuth
Telegram: https://t.me/MetaSleuthTeam




