Background
As the concept of inscriptions heats up to unprecedented levels, with prices for top inscriptions surging by tens of thousands of times, criminals have already seized the opportunity to exploit the complexity and novelty of inscriptions to perpetrate various forms of fraud, a phenomenon that is becoming increasingly rampant. These actions pose a serious threat not only to the financial security of investors but also adversely affect the healthy development of the entire inscription ecosystem. In response to this, we have meticulously outlined three typical cases of inscription attacks, including the risks of scam projects, the dangers of erroneous transfers and accidental burning, and the risks associated with centralized tools, as well as the corresponding preventative measures that users can take.
Inscription Security Risks and Countermeasures
1. Scam Project Risk
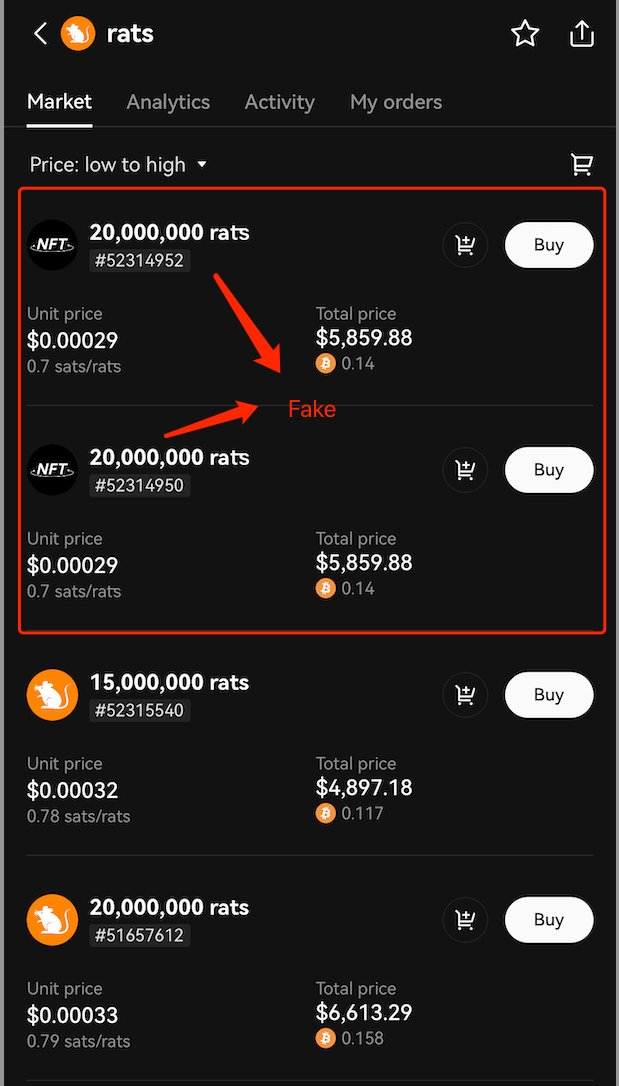
Under the current Bitcoin protocol, project identification relies primarily on the project name specified during the deployment operation, with a unique ID used to identify it in the indexer. However, ordinary users typically remember only the project's name and use it as the basis for transactions. This name-dependent method of transaction carries certain risks because there is a multitude of visually similar but different ASCII strings, which opens up opportunities for visual deception. Malicious actors can exploit these similar-looking strings to trick users into believing they are transacting with a well-known project, thereby issuing tokens for fake projects that closely resemble legitimate ones. Such scams often occur during the token minting process, where the malicious actors lead users to pay fees to acquire tokens or other virtual assets that, in reality, may be worthless. These fraudulent activities not only harm users' interests but can also cause instability in the entire ecosystem. To illustrate, let's consider a hypothetical example with a fake project named "rats." This fake "rats" is named very similarly to a legitimate one, using similar ASCII characters. If users do not carefully discern the naming, they could be misled into purchasing fake "rats" tokens, resulting in financial losses.
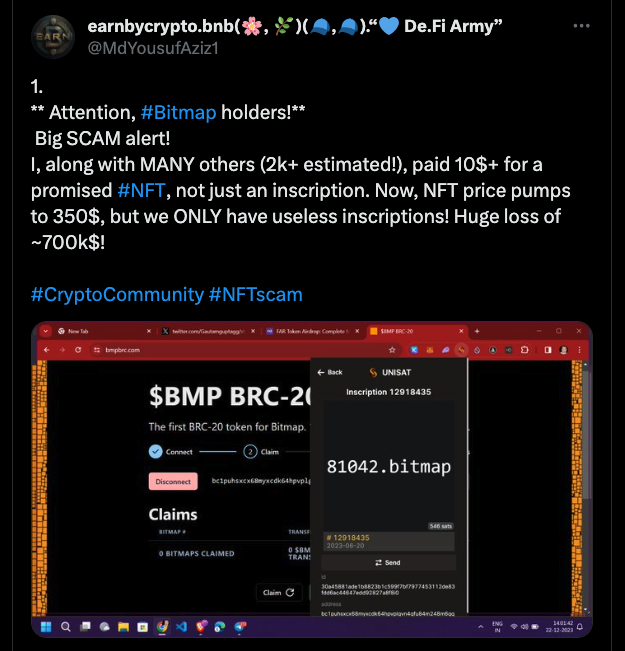
In addition to fake inscriptions, some scam inscriptions even deceive users into sending extra funds during the minting process. For instance, as shown in the image, while minting inscriptions on a bitmap, the fraudulent webpage also requests the user to make a payment to a specific address. If the user fails to notice the amount of the payment requested, they could suffer significant financial losses.
**Countermeasures: Avoid Minting Inscriptions from Unverified Sources **The channels available for minting inscriptions are quite varied, and from the types we have encountered, they include: 1. The project's own distribution website. 2. Auxiliary tools from wallets like Unisat. 3. Other third-party provided tools. These different channels for minting inscriptions can leave users confused, unable to discern the correctness and security of the channels, thus falling into the trap of scam inscriptions. We advise users to primarily use official distribution websites from wallet services or the project team to mint inscriptions. It is recommended to verify the website's authenticity before minting and to carefully review the required minting amount. For large-scale batch mints, we suggest using auxiliary tools provided by wallets to further enhance fund security.
2. Risk of Accidental Transfers and Burns
Firstly, accidental transfers refer to situations where the carrier of an inscription is treated as a normal Bitcoin during transactions. Since inscriptions are attached to Bitcoin transactions, traditional BTC wallets do not account for the additional value carried by the inscriptions and only display the value of satoshis locked in the UTXO model. Some users might conduct traditional transactions without fully understanding inscriptions. This can lead to wallets mistaking inscriptions for ordinary Bitcoin assets and merging them with other UTXOs, which are then sent to an incorrect address, resulting in irreversible losses.
Secondly, accidental burning (burn) refers to the scenario where inscriptions are destroyed or deleted because they are considered valueless or meaningless. Since inscriptions do not directly affect the ownership or value of Bitcoin in the splitting model, some users might mistakenly believe that Bitcoin carrying inscriptions are of lesser paper value, unimportant, or invalid, and choose to merge them with other UTXOs. This can result in the permanent loss of important information or assets associated with the inscriptions.
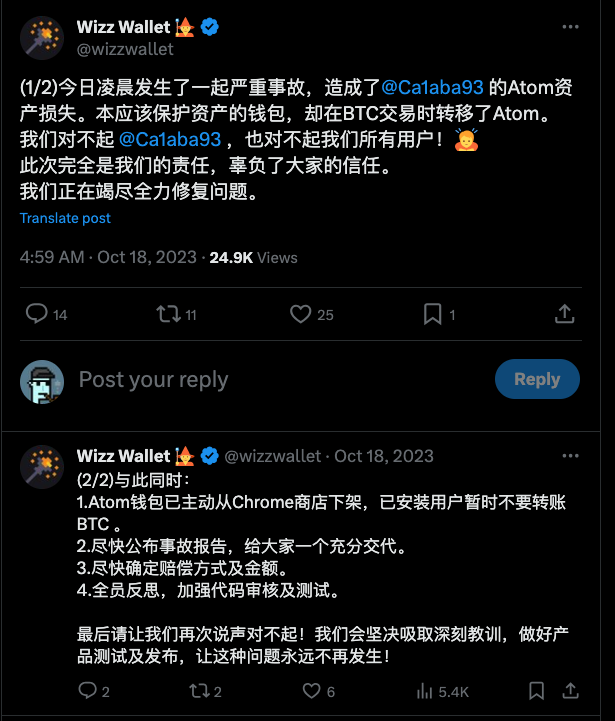
For instance, as illustrated in the image, the wallet incorrectly failed to identify the inscription within a Bitcoin transaction that should have protected it. As a result, it was treated as dust and moved out, leading to a loss.
https://twitter.com/wizzwallet/status/1714385677985661245?s=20
**Countermeasures: Prepare Dedicated Inscription Addresses and Wallets **In the splitting model, to prevent users from mistakenly transferring or burning high-value inscription assets, it is recommended that users prepare dedicated addresses and wallets specifically for their inscriptions. Such a practice can effectively reduce the risk of accidental operations and ensure the safety of inscription assets. This address should be distinct from regular transaction addresses to prevent confusion with standard Bitcoin transaction addresses. By isolating inscription transactions from other transactions, users can better control and manage their inscription assets.
3. Centralized Tool Risk
Blockchain's decentralized design allows users to directly participate in the blockchain ecosystem; however, joining the blockchain ecosystem directly via complex RPC protocols is overly complicated. As a result, the vast majority of users choose to rely on auxiliary tools to engage in the minting and trading processes within the inscription ecosystem.
Given that inscriptions are a new concept and their ecosystem is still in its infancy compared to the mature ERC20 framework, many auxiliary tools have emerged rapidly. Most of these tools focus on functional implementation while sometimes neglecting security considerations. For example, some tools may require users to import their private keys for signing transactions, or users may entrust their assets to a platform for trading purposes. These practices expose users' private keys, and centralized tools essentially control all the user's assets, which can lead to "rug pull" risks and other forms of centralized vulnerabilities. These risks are similar to cases where some wallet companies have absconded with all the user's assets after gaining access to the private keys, subsequently declaring bankruptcy.
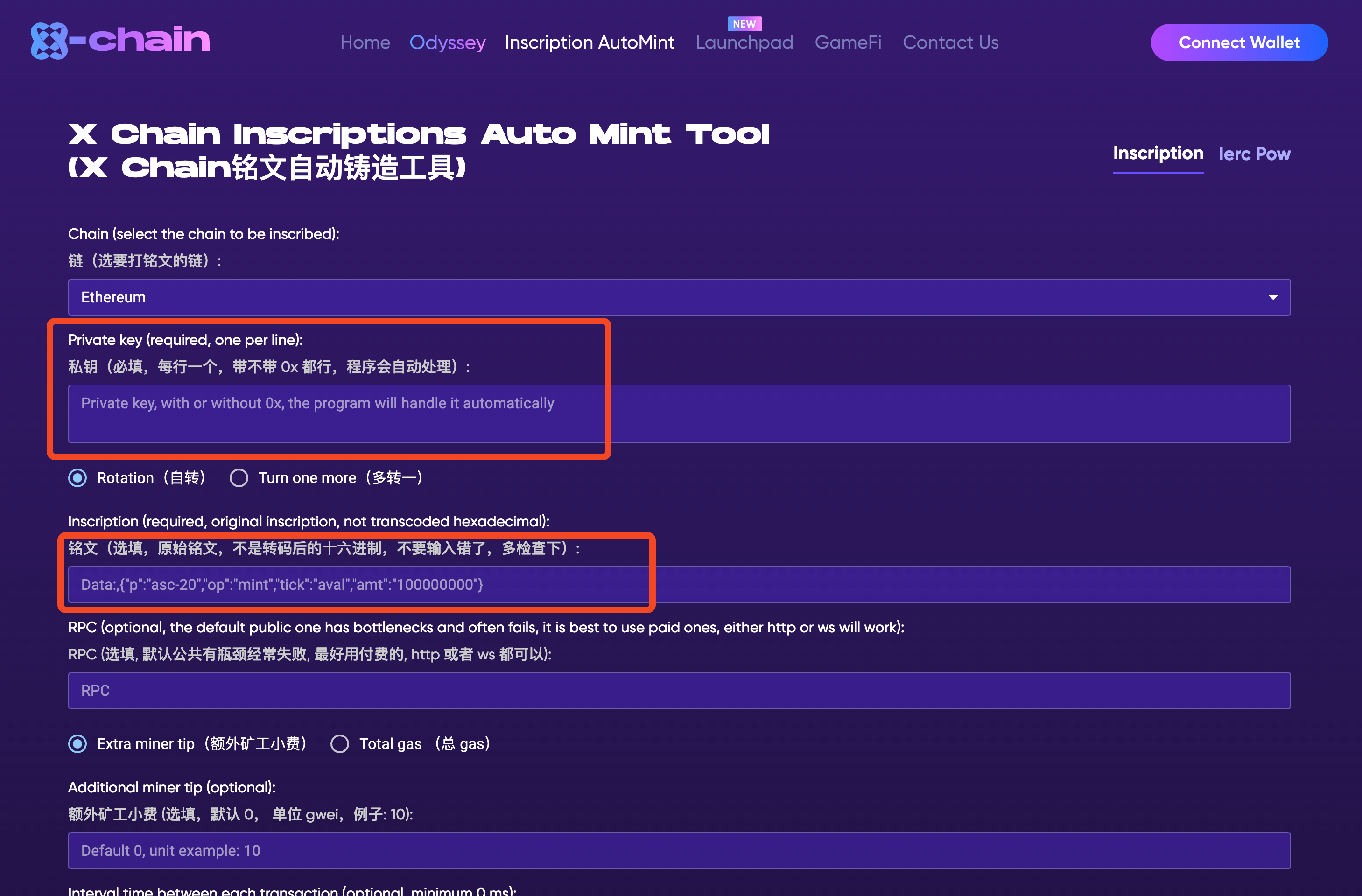
For instance, the following proxy tool steals money directly from users' wallets by obtaining their private keys.
 Countermeasures: Use Secure Inscription Auxiliary Tools
Countermeasures: Use Secure Inscription Auxiliary Tools
To enhance the security of inscription assets, users should trade and operate on well-known inscription marketplaces. For example, widely recognized inscription exploration and market platforms such as Geniidata (https://geniidata.com/Ordinals/index/brc20), Ordiscan (https://ordiscan.com/), and Etch Market (https://www.etch.market/market) provide a secure trading environment and reliable inscription information. Engaging in the minting, trading, and other operations of inscriptions on these reputable platforms can increase the security for users. Additionally, users should remain vigilant and not blindly trust inscription minting and trading services offered by unknown websites. Before performing any operations, one should thoroughly research and confirm the website's reputation and security measures. Furthermore, users must ensure they do not reveal their private keys or other sensitive information to any untrusted third parties to prevent phishing or theft incidents.
Summary
After gaining a deeper understanding of the risks associated with inscription scams, the dangers of erroneous transfers and accidental burning, and the potential threats posed by centralized tools, we can see that, although the inscription ecosystem is filled with prospects and possibilities, it also comes with numerous risks and challenges. Users must be highly vigilant and cautious regarding the transactions and storage of inscriptions. From using official channels to mint inscriptions and preparing dedicated inscription addresses and wallets, to selecting safe inscription auxiliary tools, these preventative measures can significantly reduce risks and protect the safety of users' assets. In conclusion, we encourage all users to remain cautious when participating in the inscription market; in the world of digital assets, safety is always paramount.
About MetaSleuth
MetaSleuth is a comprehensive platform developed by BlockSec to assist users in effectively tracking and investigating all crypto activities. With MetaSleuth, users can easily track funds, visualize fund flows, monitor real-time fund movements, save important information, and collaborate by sharing their findings with others. Currently, we support 13 different blockchains, including Bitcoin (BTC), Ethereum (ETH), Tron (TRX), Polygon (MATIC), and more.
Website: https://metasleuth.io/
Twitter: @MetaSleuth
Telegram: https://t.me/MetaSleuthTeam




