This blog will show how to use MetaSleuth (@MetaSleuth) to analyze a phishing attack.
Involved Addresses
For better illustration, we show the involved addresses and their abbreviations in the following.
- 0x46fbe491614e1ab6623e505e5e031ebf321cb522 (0x46fb…b522) - Possible anonymous exchange (exchange without KYC requirement)
- 0xc40a8a6763969e88c8bf58a6e7a5adc61b8ebe11 (0xc40a…be11) - Attacker-controlled address
- 0xc75368c5054d883a1923fc2d07cd2033e05a524b (0xc753…524b) - Attacker-controlled address
- 0xcc2015d66d95a3f58d8ab0c8d8bcb968212f9ebe (0xcc20…9ebe) - Possible anonymous exchange
How the Phishing Works?
The phishing website is https://leverj-cake.com. It’s a simple approval phishing.

It asks the user to approve USDT to an EOA address 0xc40a8a6763969e88c8bf58a6e7a5adc61b8ebe11.
Intelligent analysis
We then use the intelligent analysis feature of MetaSleuth to perform an analysis on 0xc40a…be11.
https://metasleuth.io/result/eth/0xc40a8a6763969e88c8bf58a6e7a5adc61b8ebe11
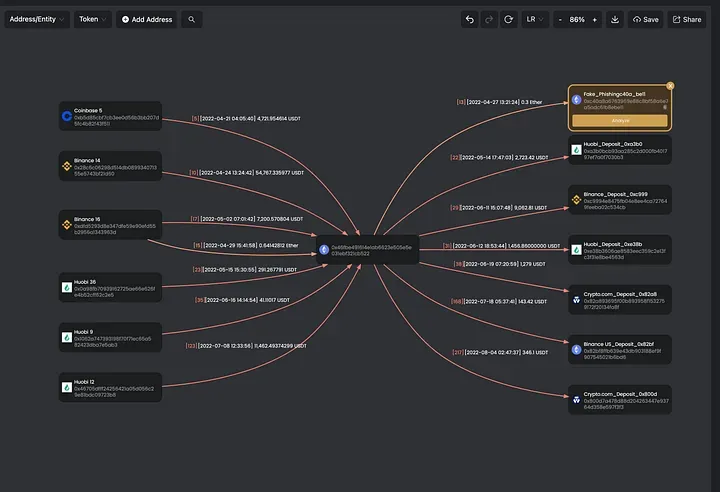
The map looks strange! The phishing address 0xc40a…be11 only has one incoming transfer from 0x46fb…b522. It has no outgoing transactions.
We then look up the transactions from Etherscan. This figure is consistent with the actual transactions.
-
First, since the phishing address 0xc40a…be11 is granted the approval permission of victim addresses, it will transfer USDT from the victim's addresses to another address 0xc753…524b, not itself. So there are no token transfers incoming from or outgoing to the phishing address.
-
Second, the incoming Ether from 0x46fb…b522 is for the gas fee to transfer the victim’s USDT.
Add new address
We then add this address (0xc753…524b) into the map and click the Analyze button to perform the analysis on this address. The map becomes complicated. If we can't find an address on the figure, we can use the Search button to search for an address. The found address will be highlighted.

Filter Addresses
We can filter the map since there are too many nodes. We can remove most incoming txs from the phishing address since they are victims. But we still leave two incoming txs because they are related to 0x46fb…b522 and 0xc40a…be11.
Question 1: Whether 0x46fb…b522 is controlled by the attacker?
We suspect that 0x46fb…b522 could be some anonymous exchange. That’s because we can see many incoming/outgoing txs of this node, some of which are from CEX exchanges.
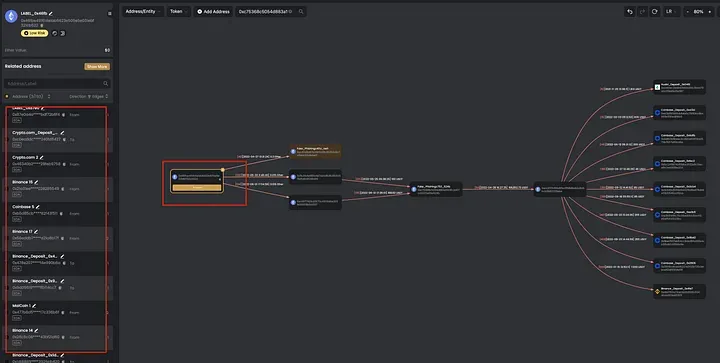
If this address 0x46fb…b522 is the anonymous exchange, then the gas fee to 0xc40a…be11 is from a anonymous exchange to hide its real identity. We can add a custom label for this address.
Question 2: Whether 0xcc20…9ebe is the address controlled by the attacker?
We found that the attacker 0xc753…524b transfers most of the profits into 0xcc20…9ebe. Note that, in the map, we merge all the same token transfers of the same direction into one edge. And the date shown on edge is the first token transfer date. We can click on the edge to show detailed transaction information between 0xc753…524b and 0xcc20…9ebe.

Click more:
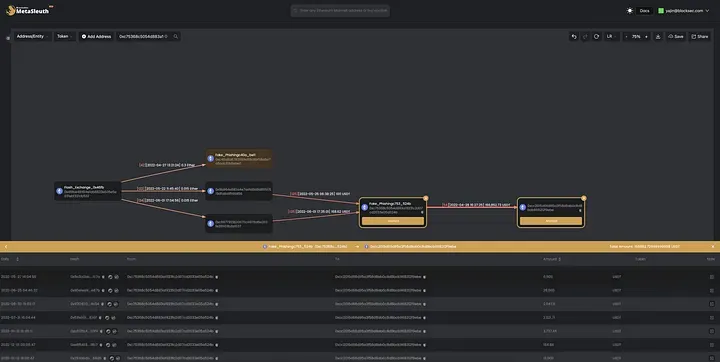
The latest transaction was on Jan 12, 2023, with 13,000 USDT.
We also found that the 0xcc20…9ebe has 83 interacted addresses, most of which are CEX addresses. We highly suspect 0xcc20…9ebe is a anonymous exchange address, not the attacker-controlled one.
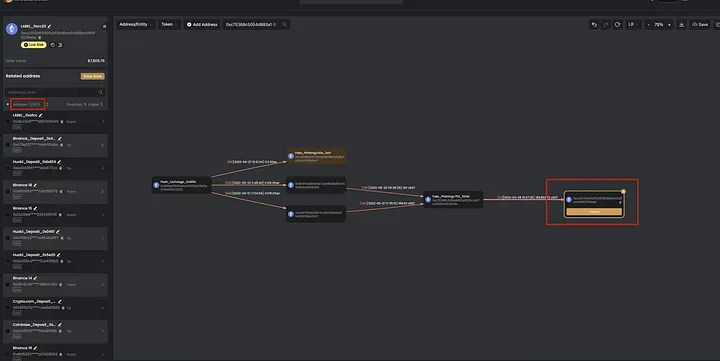
Question 3: How to get more info about the victims
Now we can add more victims on the map by clicking 0xc753…524b and using From to locate all the incoming transactions.

Interestingly, we found that 0xc753…524b also receives 0.15 Ether from the anonymous exchange address 0x46fb…b522. We believe it’s for the gas fee to transfer profits out.

Summary
From this analysis, we can conclude that:
-
The attacker uses a phishing address 0xc40a…be11 to lure users to grant the approval permission to it
-
The phishing address 0xc40a…be11 will transfer victim’s USDT to 0xc753…524b
-
The attacker periodically transfers profits into a anonymous exchange address 0xcc20…9ebe
MetaSleuth provides a fast way to analyze transactions between addresses. We can use address search, custom labels, and intelligent analysis to get a full understanding of the relationship between addresses.
We will provide more analysis examples in the future. Stay tuned.
About MetaSleuth
MetaSleuth is a comprehensive platform developed by BlockSec to assist users in effectively tracking and investigating all crypto activities. With MetaSleuth, users can easily track funds, visualize fund flows, monitor real-time fund movements, save important information, and collaborate by sharing their findings with others. Currently, we support 13 different blockchains, including Bitcoin (BTC), Ethereum (ETH), Tron (TRX), Polygon (MATIC), and more.
Website: https://metasleuth.io/
Twitter: @MetaSleuth
Telegram: https://t.me/MetaSleuthTeam




